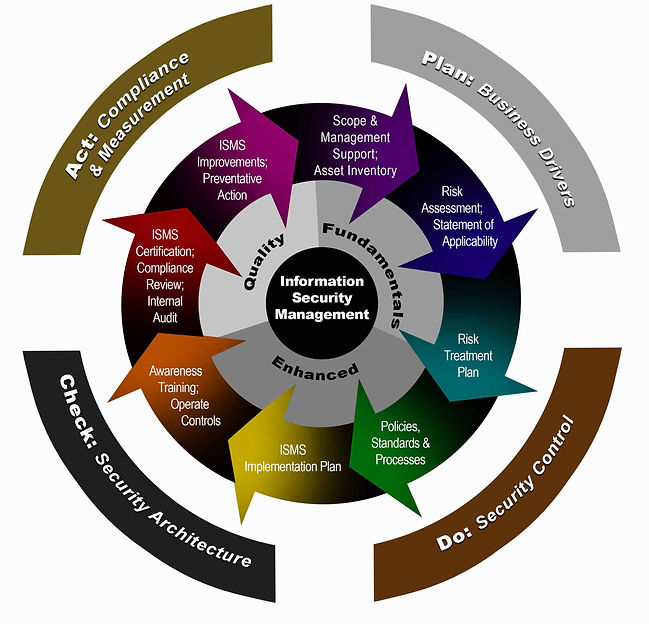
Information Security Management System (ISMS)
-
Organisational assessment: - By analysing the current Information Security environment, the effectiveness of Information Security is established. By understanding the current state environment, organisational risk areas can be identified and Information Security priorities established
-
Technical assessments and penetration testing: - the assessment includes passive scanning and information gathering, active external scanning, active internal scanning, data analysis and management reporting
-
Policy development: - Information security policies specify the measures required to protect the organisation’s information resources from all types of threats, whether internal or external, deliberate or accidental. It sets the tone and philosophy of Information Security and provides a coherent, common vision of the Information Security components within the organisation
-
Framework alignment with standards and best practices: - ISO 27001/2, (Security Management), ISO 38500, King III & CobiT (IT Governance) & ISO 20000 & ITIL, (Service Management)
-
Audit reviews: - Independent audit of the ISMS prior to final certification, security policies and strategies, ISO 20000 roadmap
-
Communication and awareness plan development: - The Plan allows for a common understanding of the activities of Information Security Management, and creates long-term support for developing and maintaining Information Security Management
IT Security Management can be scaled to suit any organisation regardless of size or complexity. No matter how large or small the organisation, there are certain controls that must be put in place in order to be able to compete in business and to comply with legislation and industry regulation.
Information is the lifeblood of all organisations and can exist in many forms. It can be printed or written on paper, stored electronically, transmitted by mail or by electronic means, shown in films, or spoken in conversation. In today's competitive business environment, such information is constantly under threat from many sources. As we move deeper into a knowledge intensive era, information continues to play a crucial role in developing the intellectual capital of an organisation. The meaning of 'enemy' has long since changed - it is no longer clear cut and certain. Enterprises today understand and emphasise more and more the importance of their information as being a valuable asset. Security in the future is about protecting transactions, information and managing business relationships. It must be the enabler to foster new ways of doing business. Companies need security solutions for the technological, organisational and cultural measures they need to implement, in order to pursue future business strategies and protect their intellectual profits. But RMS Africa understands that many information systems have not been designed to be secure. The security that can be achieved through technical means is limited, and we believe that appropriate management and procedures should support it. Confidentiality, integrity and availability of your company’s information is essential to maintain competitive edge, cash flow, profitability, legal compliance and commercial image. RMS Africa believes that a solid Information Security framework, supported by effective processes is a must for any company that wants to ensure confidentiality, integrity and availability in its business support mechanisms. There is a plethora of standards and best practices available today which provides clear guidelines on what and how that can be achieved. It also include certain limitations, such as the amount of work that is required to truly enable Information Security to safeguard the business environment from constant threats from many sources.
RMS Africa offers a unique systematic approach to help you achieve these objectives through the implementation of an Information Security Management System (ISMS), encompassing people, processes and IT systems. Implementing an ISMS offer the following business benefits
• Clarity on business drivers for Information Security Management
• More structure on Information Security
• Compliancy to international security standards, best practices, legislation and industry regulations
• Solving issues around too many security breaches
• Audit review requirements
• Role and accountability clarity
The ISMS is a systematic approach to managing sensitive company information so that it remains secure. The Framework can be considered as the highest level in the Information Security Management process. By accessing the Framework, a virtual gateway is provided to all Information Security related processes and documentation. The ISMS is a modular framework. It consists of a number of components which can be conducted and implemented as a whole or as individual components. These are described in more detail below:.